Information Climber Safety: Defending Your Information Property within the Cloud
Associated Articles
- Unlocking Your Future: A Comprehensive Guide To Finding Scholarships In 2024
- Private Loans Vs. Auto Loans: What’s The Distinction?
- Should You Take Out A Personal Loan For Vacation? A Deep Dive Into The Pros, Cons, And Alternatives
- Unlocking Higher Mortgage Charges: How To Enhance Your Credit score Rating And Get The Finest Private Mortgage Offers
- Private Loans For Retirees: Navigating The Choices And Dangers
Introduction
Welcome to our in-depth have a look at Information Climber Safety: Defending Your Information Property within the Cloud
Information Climber Safety: Defending Your Information Property within the Cloud
The cloud has turn into the muse of contemporary enterprise, providing unparalleled scalability, flexibility, and cost-efficiency. Nonetheless, this digital panorama additionally presents distinctive safety challenges, demanding a proactive and complete strategy to safeguard your treasured information property.
This text delves into the world of "Information Climber Safety", a holistic framework designed to safe your information within the cloud, very like a talented climber navigates treacherous terrain. We’ll discover the important thing rules, methods, and applied sciences that empower you to guard your information from the ever-evolving threats of the digital age.
Understanding the Cloud Safety Panorama
The cloud, whereas providing immense benefits, introduces a definite set of safety issues. Not like conventional on-premises techniques, the place bodily safety is paramount, cloud safety focuses on:
- Shared Accountability Mannequin: Cloud suppliers are accountable for securing the underlying infrastructure, whilst you, the shopper, are accountable for securing your information and purposes working on that infrastructure. This shared accountability mannequin requires clear understanding and communication to make sure efficient safety.
- Distributed Structure: Cloud environments are sometimes extremely distributed, with information and purposes unfold throughout a number of places and interconnected by way of complicated networks. This complexity provides layers of challenges for safety administration and monitoring.
- Dynamic Environments: Cloud sources could be provisioned and de-provisioned quickly, making a dynamic panorama that requires fixed adaptation and monitoring to make sure safety stays intact.
- Information Accessibility: Cloud environments typically contain sharing information with third-party purposes and companies, requiring cautious consideration of information entry controls and encryption methods.

Information Climber Safety: A Holistic Method
Information Climber Safety adopts a multi-faceted strategy, encompassing the next key rules:
1. Basis: Safe Infrastructure and Entry Management
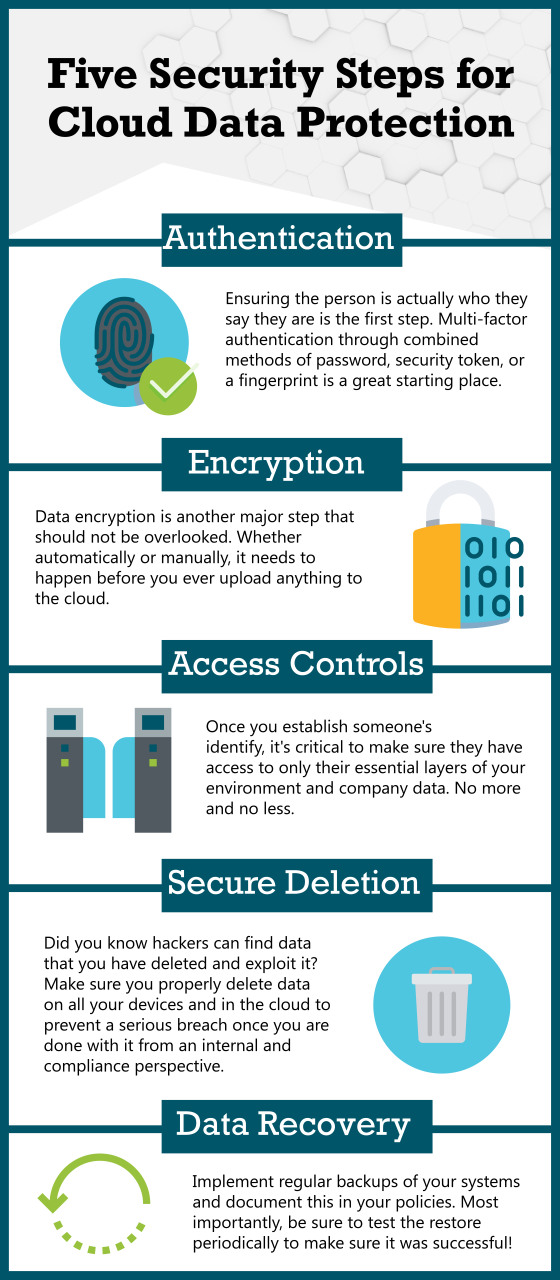
- Sturdy Authentication: Implementing multi-factor authentication (MFA) for all person accounts, together with privileged accounts, is essential. This provides an additional layer of safety by requiring customers to offer a number of types of identification, making it considerably tougher for unauthorized people to realize entry.
- Least Privilege Precept: Granting customers solely the minimal permissions essential to carry out their duties is important. This minimizes the potential impression of a safety breach, as compromised accounts can have restricted entry to delicate information.
- Sturdy Community Safety: Implementing firewalls, intrusion detection techniques (IDS), and intrusion prevention techniques (IPS) to watch and block malicious visitors is significant. Safe community segmentation can additional isolate delicate information and purposes from potential threats.
- Common Safety Audits: Conducting common safety audits helps determine vulnerabilities and misconfigurations that may very well be exploited by attackers. These audits ought to cowl all facets of the cloud infrastructure, together with entry controls, community safety, and software safety.
2. Ascend: Information Safety and Encryption
- Information Encryption at Relaxation: Encrypting information saved within the cloud, each at relaxation and in transit, is prime. Encryption ensures that even when information is stolen, it stays unreadable with out the suitable decryption keys.
- Information Encryption in Transit: Encrypting information throughout transmission between varied cloud parts and purposes is essential to forestall eavesdropping and information interception. This may be achieved by way of protocols like TLS/SSL.
- Information Loss Prevention (DLP): Implementing DLP options helps forestall delicate information from leaving the cloud setting with out authorization. These options can monitor information stream, determine delicate data, and block unauthorized transfers.
- Information Masking and Tokenization: Changing delicate information with non-sensitive substitutes, similar to masked values or tokens, can defend information from unauthorized entry and use.
3. Summit: Monitoring and Risk Intelligence
- Actual-time Monitoring: Steady monitoring of cloud infrastructure and purposes is important for detecting and responding to safety threats in real-time. This contains monitoring community visitors, person exercise, and system logs.
- Safety Info and Occasion Administration (SIEM): Implementing a SIEM answer centralizes safety information from varied sources, offering complete visibility and enabling real-time menace detection and response.
- Risk Intelligence: Staying knowledgeable concerning the newest threats and vulnerabilities is essential. Using menace intelligence feeds and collaborating with safety communities gives insights into rising assault vectors and helps proactively mitigate dangers.
- Incident Response Planning: Growing a strong incident response plan outlines the steps to soak up case of a safety breach. This plan ought to embody procedures for containment, investigation, restoration, and communication.
4. Descent: Governance and Compliance
- Cloud Safety Posture Administration (CSPM): Using CSPM instruments helps repeatedly assess and enhance cloud safety posture. These instruments present insights into vulnerabilities, misconfigurations, and compliance gaps.
- Cloud Safety Compliance: Adhering to related business requirements and laws, similar to ISO 27001, SOC 2, and HIPAA, is essential for sustaining information safety and belief.
- Common Safety Coaching: Offering common safety coaching to workers helps elevate consciousness about frequent threats, greatest practices, and safety insurance policies. This fosters a tradition of safety throughout the group.
- Information Backup and Restoration: Implementing strong information backup and restoration methods is important to make sure information availability within the occasion of a safety breach or catastrophe. Often testing backups and restoration procedures is essential to make sure their effectiveness.
Key Applied sciences for Information Climber Safety
A number of applied sciences play a pivotal function in attaining Information Climber Safety:
- Cloud Entry Safety Dealer (CASB): CASBs act as safety gateways between customers and cloud purposes, imposing safety insurance policies and monitoring information entry. They supply visibility into cloud utilization, management information entry, and defend delicate information.
- Cloud Safety Posture Administration (CSPM): CSPM instruments repeatedly assess cloud safety posture by figuring out vulnerabilities, misconfigurations, and compliance gaps. They supply suggestions for remediation and assist keep a safe cloud setting.
- Safety Info and Occasion Administration (SIEM): SIEM options centralize safety information from varied sources, offering complete visibility into safety occasions. They allow real-time menace detection, incident response, and safety analytics.
- Cloud Workload Safety Platforms (CWPP): CWPPs present complete safety for cloud workloads, together with containerized purposes and serverless capabilities. They provide runtime safety, menace detection, and vulnerability administration for cloud-native purposes.
- Cloud Native Safety Info and Occasion Administration (CN-SIEM): CN-SIEMs are particularly designed for cloud environments, offering real-time visibility into cloud safety occasions and enabling efficient menace detection and response.
Greatest Practices for Information Climber Safety
- Undertake a Zero Belief Safety Mannequin: Assume that no person or system could be trusted by default. This strategy requires verifying each request and imposing least privilege entry insurance policies.
- Implement Sturdy Password Insurance policies: Encourage customers to create sturdy, distinctive passwords for every cloud account and implement common password modifications.
- Use Encryption for All Information: Encrypt all information at relaxation and in transit, no matter sensitivity degree. This ensures that even when information is compromised, it stays unreadable.
- Often Patch Methods: Hold all cloud infrastructure and purposes up-to-date with the most recent safety patches to deal with vulnerabilities.
- Monitor Cloud Safety Posture: Constantly monitor cloud safety posture, determine vulnerabilities, and take rapid motion to remediate them.
- Conduct Common Safety Audits: Conduct periodic safety audits to determine weaknesses and guarantee compliance with safety requirements.
- Practice Workers on Safety Greatest Practices: Present common safety coaching to workers to lift consciousness about frequent threats and greatest practices.
- Develop a Sturdy Incident Response Plan: Create an in depth incident response plan outlining steps to soak up case of a safety breach.
- Collaborate with Cloud Suppliers: Work intently with cloud suppliers to leverage their safety experience and guarantee compliance with their safety pointers.
The Way forward for Information Climber Safety
Because the cloud panorama continues to evolve, Information Climber Safety should adapt to satisfy new challenges. Rising applied sciences like synthetic intelligence (AI) and machine studying (ML) will play a vital function in enhancing cloud safety:
- AI-Powered Risk Detection: AI algorithms can analyze huge quantities of safety information to determine anomalies and potential threats in real-time. This might help organizations proactively detect and reply to assaults earlier than they trigger important harm.
- Automated Safety Response: AI and ML can automate safety duties similar to incident response, vulnerability patching, and menace mitigation, liberating up safety groups to give attention to extra strategic initiatives.
- Cloud Safety Posture Optimization: AI-powered instruments can analyze cloud environments to determine safety gaps and recommend enhancements, serving to organizations optimize their cloud safety posture.
- Zero Belief Safety Automation: AI and ML can automate the implementation and enforcement of zero belief safety rules, making certain that solely approved customers and units have entry to delicate information.
Conclusion
Information Climber Safety is a vital framework for shielding your helpful information property within the cloud. By embracing a holistic strategy that encompasses safe infrastructure, information safety, monitoring, and governance, you possibly can successfully mitigate dangers and safeguard your group’s digital property.
Because the cloud panorama continues to evolve, staying knowledgeable about rising threats and leveraging new applied sciences will likely be essential for sustaining strong Information Climber Safety. By adopting a proactive and adaptive strategy, you possibly can be certain that your information stays safe and your enterprise thrives within the digital age.
Bear in mind, Information Climber Safety isn’t a vacation spot, however a journey. It requires steady vigilance, adaptation, and collaboration to make sure that your information stays protected within the ever-changing cloud setting.
Closure
We hope this text has helped you perceive the whole lot about Information Climber Safety: Defending Your Information Property within the Cloud. Keep tuned for extra updates!
Ensure to comply with us for extra thrilling information and critiques.
Be happy to share your expertise with Information Climber Safety: Defending Your Information Property within the Cloud within the remark part.
Hold visiting our web site for the most recent developments and critiques.