Securing Your Knowledge: Defending Data Utilizing Knowledge Climber Options
Associated Articles
- Emergency Private Loans: Your Monetary Lifeline When You Want It Most
- Unlocking Your Potential: Scholarships For Non-Conventional College students
- Achieving Compliance With Data Climber: Data Governance Best Practices
- Unlocking Your Financial Goals: A Comprehensive Guide To Joint Personal Loans
- Cracking The Code: How To Finance Your Law School Dreams With Scholarships
Introduction
Be a part of us as we discover Securing Your Knowledge: Defending Data Utilizing Knowledge Climber Options, full of thrilling updates
Securing Your Knowledge: Defending Data Utilizing Knowledge Climber Options
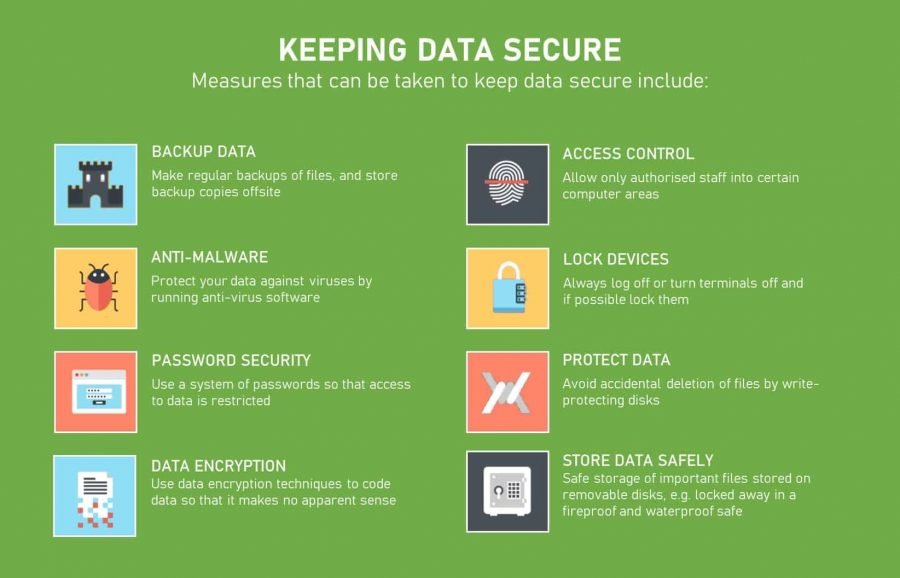
In at this time’s digital panorama, knowledge is the lifeblood of companies, organizations, and people. From delicate monetary information to confidential medical data, the worth of knowledge is simple. Nevertheless, this similar worth makes it a major goal for cybercriminals, who’re continuously searching for methods to steal, exploit, and compromise it. Because of this, knowledge safety has turn into a paramount concern, demanding strong and revolutionary options to guard our digital property.
One such resolution is Knowledge Climber, a revolutionary strategy to knowledge safety that makes use of a novel mixture of superior applied sciences and methodologies. This text delves into the world of Knowledge Climber, exploring its core rules, functionalities, and advantages in securing your knowledge. We’ll additionally look at real-world situations the place Knowledge Climber has confirmed its effectiveness, showcasing its potential to safeguard your data from even probably the most refined cyber threats.
Understanding the Knowledge Climber Strategy
Knowledge Climber is just not a single product however fairly a complete framework that encompasses a spread of instruments, strategies, and methods designed to guard knowledge at each stage of its lifecycle. At its core, Knowledge Climber operates on the precept of knowledge minimization, which emphasizes the significance of solely gathering and storing the information that’s completely essential for a selected function. This precept helps cut back the potential assault floor, minimizing the danger of knowledge breaches.
Knowledge Climber’s Key Elements:
-
Knowledge Discovery and Classification: Step one in securing knowledge is to establish and perceive what knowledge you’ve got. Knowledge Climber employs refined knowledge discovery instruments to scan your programs and databases, figuring out all delicate data. This data is then categorised primarily based on its sensitivity stage, permitting you to prioritize safety efforts accordingly.

Entry Management and Authorization: As soon as knowledge is recognized and categorised, Knowledge Climber implements strong entry management mechanisms to make sure that solely licensed people can entry it. This includes implementing granular entry permissions primarily based on person roles, knowledge sensitivity, and particular enterprise wants.
-
Knowledge Encryption: Knowledge encryption is a elementary safety measure that transforms knowledge into an unreadable format, rendering it inaccessible to unauthorized events. Knowledge Climber makes use of industry-leading encryption algorithms to guard knowledge each at relaxation and in transit, guaranteeing that even when knowledge is compromised, it stays unreadable.
-
Knowledge Masking and Tokenization: For conditions the place knowledge must be shared or accessed for particular functions, Knowledge Climber employs knowledge masking and tokenization strategies. These strategies exchange delicate knowledge with non-sensitive substitutes, successfully obscuring the unique data whereas preserving its performance.
-
Knowledge Loss Prevention (DLP): Knowledge Climber consists of strong knowledge loss prevention mechanisms that monitor and management the stream of delicate knowledge inside your group. This helps stop unintentional or malicious knowledge leakage via numerous channels, akin to e mail, file sharing, and cloud storage.
-
Safety Monitoring and Risk Detection: Steady monitoring is essential for figuring out and responding to potential threats. Knowledge Climber makes use of superior safety monitoring instruments to detect suspicious actions and anomalies in real-time, permitting for immediate incident response and mitigation.
-
Knowledge Governance and Compliance: Knowledge Climber helps organizations set up and preserve a strong knowledge governance framework, guaranteeing compliance with related knowledge privateness rules akin to GDPR, HIPAA, and CCPA. This includes implementing insurance policies, procedures, and controls to handle knowledge all through its lifecycle.
Advantages of Implementing Knowledge Climber Options
Implementing Knowledge Climber options brings quite a few advantages to organizations, together with:
- Enhanced Knowledge Safety: By implementing a complete knowledge safety framework, Knowledge Climber considerably reduces the danger of knowledge breaches and compromises.
- Improved Compliance: Knowledge Climber helps organizations adjust to numerous knowledge privateness rules, minimizing the danger of fines and penalties.
- Lowered Operational Prices: By minimizing knowledge storage and administration overhead, Knowledge Climber may also help organizations optimize their IT infrastructure and cut back operational prices.
- Enhanced Enterprise Agility: Knowledge Climber’s versatile and scalable options allow organizations to shortly adapt to altering enterprise wants and regulatory necessities.
- Elevated Buyer Belief: By demonstrating a dedication to knowledge safety, organizations can construct belief with their clients and companions.
Actual-World Examples of Knowledge Climber Success
Knowledge Climber options have been efficiently carried out throughout numerous industries, demonstrating their effectiveness in defending delicate data. Listed below are some real-world examples:
Healthcare: A number one healthcare supplier carried out Knowledge Climber to safe affected person well being information, guaranteeing compliance with HIPAA rules. The answer helped them obtain granular entry management, encrypt affected person knowledge, and implement strong knowledge loss prevention measures.
Monetary Companies: A serious monetary establishment adopted Knowledge Climber to guard buyer monetary knowledge, together with bank card data and account particulars. The answer’s superior encryption and knowledge masking options helped them safeguard delicate knowledge from unauthorized entry.
Authorities: A authorities company accountable for dealing with delicate nationwide safety data carried out Knowledge Climber to safe its knowledge facilities and significant infrastructure. The answer’s complete safety monitoring and menace detection capabilities helped them establish and reply to cyber threats in real-time.
Training: A college carried out Knowledge Climber to guard pupil information and analysis knowledge. The answer’s entry management mechanisms and knowledge encryption capabilities helped them adjust to FERPA rules and make sure the privateness of pupil data.
Case Research: Defending Delicate Knowledge within the Retail Business
A big retail firm confronted the problem of defending buyer knowledge, together with private data, buy historical past, and cost particulars, from cyber threats. They had been involved in regards to the potential for knowledge breaches, which might harm their popularity and result in important monetary losses.
To deal with these issues, the corporate carried out Knowledge Climber options, which included:
- Knowledge Discovery and Classification: Knowledge Climber instruments recognized all buyer knowledge saved throughout numerous programs and databases, classifying it primarily based on its sensitivity stage.
- Entry Management and Authorization: The corporate carried out granular entry controls, guaranteeing that solely licensed workers might entry particular buyer knowledge primarily based on their roles and tasks.
- Knowledge Encryption: Knowledge Climber encrypted all buyer knowledge each at relaxation and in transit, rendering it unreadable to unauthorized events.
- Knowledge Masking and Tokenization: For particular enterprise processes that required knowledge sharing, the corporate utilized knowledge masking and tokenization strategies to interchange delicate knowledge with non-sensitive substitutes.
- Knowledge Loss Prevention (DLP): Knowledge Climber’s DLP mechanisms monitored and managed the stream of delicate knowledge, stopping unintentional or malicious knowledge leakage via numerous channels.
- Safety Monitoring and Risk Detection: Knowledge Climber’s superior safety monitoring instruments constantly scanned for suspicious actions and anomalies, permitting the corporate to answer potential threats in real-time.
On account of implementing Knowledge Climber options, the retail firm considerably enhanced its knowledge safety posture. They had been in a position to cut back the danger of knowledge breaches, adjust to knowledge privateness rules, and construct belief with their clients.
Conclusion
In at this time’s data-driven world, securing your data is paramount. Knowledge Climber presents a complete and efficient resolution that addresses the ever-evolving threats to knowledge safety. By implementing its superior applied sciences and methodologies, organizations can shield their most beneficial property, guaranteeing compliance, lowering operational prices, and constructing belief with their stakeholders.
Past Knowledge Climber: A Holistic Strategy to Knowledge Safety
Whereas Knowledge Climber offers a strong framework for knowledge safety, it is important to keep in mind that knowledge safety is a holistic endeavor that requires a multi-layered strategy. Listed below are some further concerns:
- Worker Training and Consciousness: Coaching workers on greatest practices for knowledge safety, together with password hygiene, phishing consciousness, and safe knowledge dealing with, is essential.
- Common Safety Audits and Assessments: Conducting common safety audits and assessments helps establish vulnerabilities and weaknesses in your safety posture.
- Incident Response Plan: Having a well-defined incident response plan helps organizations shortly and successfully reply to knowledge breaches and different safety incidents.
- Collaboration and Data Sharing: Collaborating with different organizations and sharing menace intelligence may also help strengthen your general safety posture.
By adopting a complete strategy to knowledge safety, organizations can create a strong protection towards cyber threats and safeguard their precious knowledge property. Knowledge Climber, with its revolutionary applied sciences and methodologies, performs an important function on this journey, empowering organizations to confidently navigate the digital panorama and shield their knowledge within the face of ever-increasing cyber threats.
Closure
Thanks for studying! Stick with us for extra insights on Securing Your Knowledge: Defending Data Utilizing Knowledge Climber Options.
Ensure to observe us for extra thrilling information and opinions.
Be happy to share your expertise with Securing Your Knowledge: Defending Data Utilizing Knowledge Climber Options within the remark part.
Keep knowledgeable with our subsequent updates on Securing Your Knowledge: Defending Data Utilizing Knowledge Climber Options and different thrilling subjects.